Simplify user security anywhere with automated, integrated ZTNA
Today’s professionals are on the move, and they could be logging in from the office or the airport. Traditional perimeter-based security models can’t handle that kind of pressure and uncertainty. That’s why more organizations are turning to Zero Trust Network Access (ZTNA) — a modern security approach built on the principle of “never trust, always verify.”
The concept of ZTNA has been around since 2010. Early implementations faced challenges such as high complexity and administrative overhead, but advances in technology have put this type of security within reach for most businesses. IT professionals are increasingly adopting the ZTNA model to keep their users connected and secure wherever they may be.
Before we get too far, let’s further explore a few key elements of ZTNA:
- User authentication – Verifies user identity using strong methods (e.g., MFA, SSO)
- Device verification – Ensures the device is authorized and meets security standards
- Least-privilege access – Grants users access only to the resources they need
- Micro segmentation – Limits lateral movement by segmenting access at the application level
- Continuous monitoring – Continuously verifies trust based on behavior, location and risk
- Policy-based access control – Uses dynamic, context-aware rules to enforce access decisions
- Encrypted connections – Secures data in transit through end-to-end encryption
- Application-level access – Provides access to specific applications, not the full network
ZTNA = Device posture check + Least privilege access + User identity
Building your ZTNA framework
Here are the essential components you need to build a strong, scalable ZTNA foundation that keeps users connected and your data protected. Let’s explore how you can find them.
Continuous device posture check
Implementing device-specific access control policies is essential to prevent unpatched or vulnerable devices from connecting. However, continuous monitoring of device posture is critical in today’s high-stakes security landscape. When suspicious behavior is detected, access can be revoked in real time.
Datto Secure Edge addresses this need with SafeCheck, a continuous device posture check integrated with Datto RMM. This powerful combination unites best-of-breed access control and remote management solutions to enhance your security posture.
Least privileged access
Zero Trust principles of least privileged access are enforced through granular access controls. Datto Secure Edge empowers IT administrators to precisely control user and device permissions, ensuring they only access the resources necessary for their roles. This approach significantly reduces risk and strengthens overall security.
User identity and MFA
A true ZTNA strategy depends on robust user authentication and authorization. Adding multifactor authentication (MFA) provides a critical additional layer of protection, blocking unauthorized access even if credentials are compromised. However, security should never come at the cost of complexity or inflexibility.
Datto Secure Edge seamlessly integrates with Microsoft Entra ID and Google Identity for authentication, as well as popular MFA solutions like Cisco Duo and Okta. With Secure Edge, implementing strong security is straightforward and user-friendly for security that’s a snap, not a burden.[AN2]
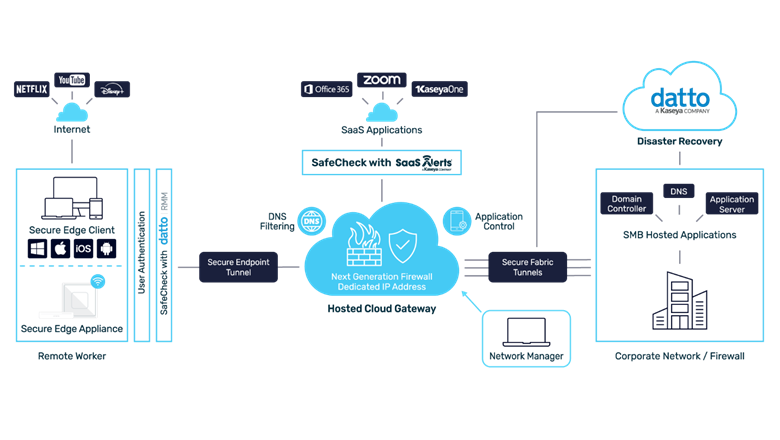
Device posture check with Datto RMM
To safeguard user security and protect corporate data, it is vital to keep devices managed, patched and secure. SafeCheck with Datto RMM provides continuous enforcement, ensuring that only trusted users and devices can access the network. This approach significantly reduces the risk of security threats and unauthorized access, strengthening overall network and data protection. As a result, IT teams gain greater confidence and peace of mind when managing remote users.
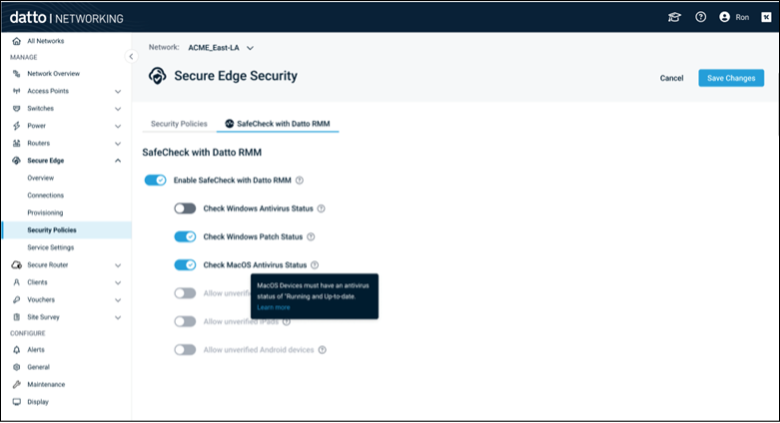
Securing Microsoft 365
Implementing a ZTNA strategy requires establishing least-privileged access controls. However, applying these controls can be complex and time-consuming. The SaaS Alerts Fortify module helps you efficiently improve the security posture across all your Microsoft 365 tenants.
By integrating Secure Edge SafeCheck with SaaS Alerts, the process is automated: The static IP address of the Secure Edge Gateway is shared with a predefined list of users and incorporated into your Microsoft 365 conditional access policies. This seamless integration empowers IT administrators to strengthen security without added complexity, saving time and simplifying the enforcement of least privileged access.
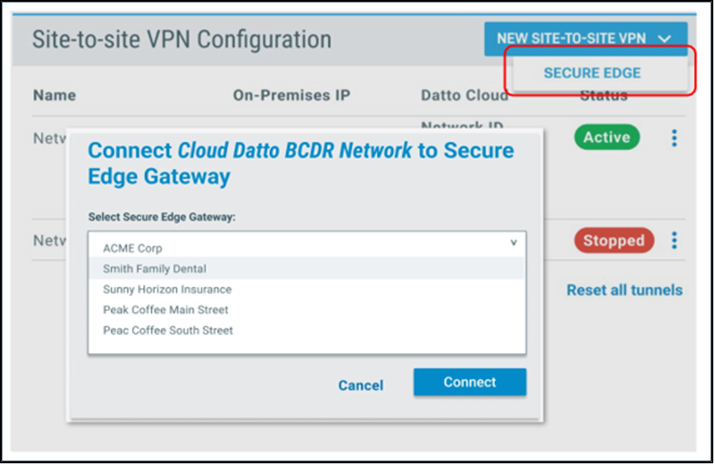
Disaster recovery
When disaster strikes, every second counts. With just a few clicks, Secure Edge enables users to quickly and securely connect to your BCDR Cloud recovery systems, dramatically improving recovery time. This streamlined process minimizes the time and effort needed to configure connections, helping your team get back to work faster.
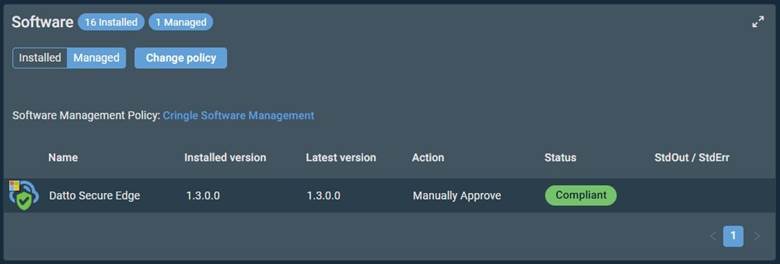
Software management
Managing software can be complex and time-consuming, yet it’s essential for keeping your endpoints secure and up to date. Kaseya offers two powerful remote monitoring and management (RMM) tools: VSA 10 and Datto RMM. Both feature automated, policy-driven frameworks to ensure software and endpoints remain current.
Secure Edge is fully integrated with both VSA 10 and Datto RMM. Following the release of the latest Secure Edge software, updated versions will be available in the VSA 10 and Datto RMM catalogs, enabling you to easily deploy and manage updates across your systems.
Automated tickets
Secure Edge is already integrated with Kaseya’s two PSA tools, BMS and Autotask. Once integrated, any alerts from Secure Edge can automatically generate new PSA tickets for your IT staff. This out-of-the-box integration streamlines the deployment process, reducing the steps needed to get Secure Edge up and running.
Inventory management
Secure Edge can be deployed with an optional DSE appliance that broadcasts the same Wi-Fi SSID used in the office, making transitions between in-office and work-from-home days seamless. Managing these Secure Edge appliances is effortless thanks to the automated inventory management of Datto Networking devices, including the Secure Edge Appliance.
Integrated billing
Billing accuracy is paramount, errors and time-consuming reconciliation can be costly to your business. That’s why all Datto Network and Secure Edge subscriptions are automatically synced with BMS and Autotask. Save time and reduce billing errors by setting up Integrated Customer Billing today with Autotask and BMS.
Datto Secure Edge makes implementing ZTNA easy
Adopting a Zero Trust approach is no longer optional. Datto Secure Edge empowers IT teams to confidently protect their networks and data while also reducing administrative overhead. If you’re ready to strengthen your security posture, streamline compliance, and gain peace of mind managing remote and hybrid environments, Datto Secure Edge is the foundation you can trust. Learn more.




