Ransomware is inevitable, data loss isn’t: Ensure recovery without paying ransom
Ransomware is the biggest threat businesses face today. What began as isolated opportunistic attacks has evolved into a multibillion-dollar criminal enterprise driven by a sophisticated underground economy.
The ransomware ecosystem is now highly structured, mirroring the operations of legitimate industries. At the core of it are malware developers who build ransomware payloads, counter-antivirus tools and crypting services. Meanwhile, infrastructure providers offer bulletproof hosting and anonymous virtual private networks (VPNs) to facilitate attacks. Communication between threat actors happens through darknet forums and encrypted messaging platforms. On the financial side, cash-out services, mixers and laundering networks move ransom payments across borders with minimal traceability. Today, even individuals with limited technical expertise can execute high-impact attacks using Ransomware-as-a-Service (RaaS) kits that come with ready-made tools and support.
This evolving threat landscape puts intense pressure on MSPs and internal IT teams. SMBs are now treated as low-hanging fruit and have become prime targets for cybercriminals. While threat actors leverage double and even triple extortion techniques to target SMBs, what SMBs often have in response are traditional backup strategies that fall far short.
In this blog, we’ll explore why backup strategies are falling short against today’s ransomware threats. We’ll bust some of the most common myths that put businesses at risk and discuss why recovery — and not ransom payment — is the only way out. Along the way, we’ll also see how Datto helps you build ransomware resilience and stay aligned with cyber insurance and compliance requirements.
Myth-busting: Why many backup strategies fail against ransomware
Let’s bust some of the most common backup myths that could be putting your data — or your clients’ data — at serious risk. These assumptions often create a false sense of security, leaving businesses vulnerable when ransomware strikes.
Backup myth 1: Cloud = safe
It’s easy to see why this myth exists. Early ransomware strains mostly affected only the infected device, rarely reaching beyond the local system. However, those days are long gone.
Modern ransomware is much more advanced. It actively seeks out connected environments and can encrypt data stored in popular Software-as-a-Service (SaaS) platforms like Microsoft 365 and Google Workspace. Even cloud infrastructure, such as Microsoft Azure, is now in the crosshairs.
If a remote employee’s device is compromised, that infection can quickly spread to shared cloud drives and synced folders. Suddenly, the cloud isn’t a backup anymore but a part of the blast radius.
Backup myth 2: “We’ll just restore from a backup.”
Restoring from backups sounds like a simple solution, but in reality, it usually isn’t enough. Attackers know that businesses rely on backups, so they’ve adapted their tactics. Modern ransomware is designed to cripple recovery by planting time bombs, corrupting backup repositories, encrypting files in phases or introducing long delays before triggering.
Imagine this: ransomware quietly enters your network and stays dormant for months like a hidden time bomb. It slips past detection, gets backed up along with your clean data and waits. If your retention policy only stores backups for three months but the ransomware detonates after four, every restore point is compromised. At that stage, recovery is no longer an option and paying the ransom may feel like the only way out.
Myth 3: Paying ransom guarantees recovery
Paying the ransom might seem like the fastest way to get data back. However, it’s a high-stakes gamble. Research from the Ponemon Institute found that only 13% of organizations that paid attackers recovered all their data. Many received only partial or corrupted files, if any.
The risks don’t stop there. Once a ransom is paid, criminals often return with new demands or reinfect systems using hidden backdoors. Even in cases where data is returned, payment doesn’t solve the underlying problem. Businesses still face extended downtime, the expense of remediation and the challenge of rebuilding trust with customers and partners. On top of that, it also complicates both cyber insurance claims and regulatory compliance.
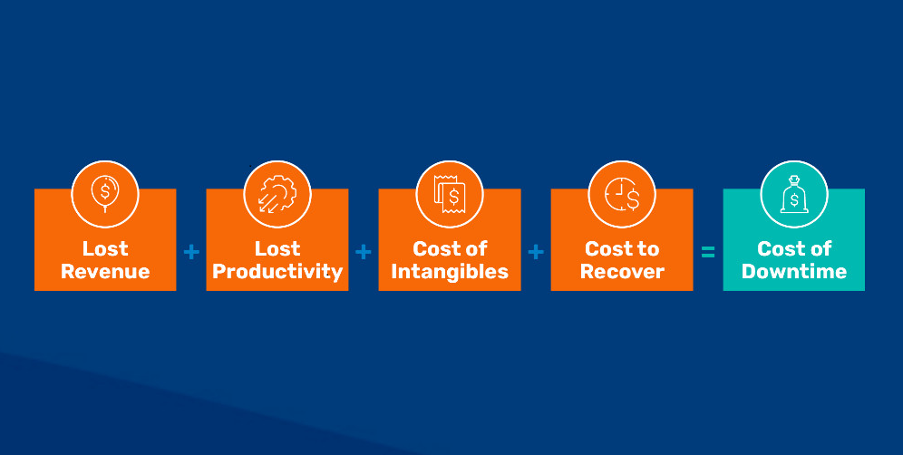
Fig 1: The total cost of downtime
Building the foundation of true ransomware resilience
Recovery — not ransom — is the only reliable solution to ransomware threats. To make recovery possible, businesses need a solid foundation of resilience built on two crucial pillars: immutable backups and tested, clean restore points.
Immutable backups are at the heart of ransomware resilience. With immutable storage, backup data cannot be altered or deleted by ransomware, ensuring recovery points remain intact. Frequent, verified backups reduce the risk of significant data loss, giving you a much shorter window of vulnerability. And by replicating backups off-site, businesses gain an extra layer of protection, maintaining access to clean data even in the event of a site-wide outage.
Just as immutable backups protect data from being altered, recovery depends on having restore points you know you can trust. A backup is only as good as its ability to be restored, which is why regular testing is essential. You must be able to spin up backups away from production, validate application behavior and confirm that data is intact before anything returns to your network. Adding to it, in-built mechanisms like integrated ransomware detection that watch for abnormal patterns in your backup data, you can prevent reinfection and ensure that every approved restore point is truly clean and ready for use.
How Datto delivers purpose-built ransomware resilience
A ransomware attack can cause severe disruption for any IT team. For internal teams, it can mean halted operations, mounting downtime costs and pressure from every corner of the business to get systems back online. For MSPs, the stakes are even higher. Managing multiple client environments means a single incident has the power to derail your entire operation. Suddenly, your team is pulled off billable projects to handle the crisis. Service-level agreements (SLAs) for other clients start to slip. Margins shrink, trust erodes and credibility suffers.
To withstand today’s ransomware threats, you need a platform designed for resilience, not one retrofitted after the fact. And that’s exactly what Datto delivers. Every layer of Datto’s Business Continuity and Disaster Recovery (BCDR) solution is engineered to anticipate modern attack tactics and provide MSPs and internal IT teams with fast, reliable recovery.
With Datto, you get:
- Hardened Linux-based appliances: Datto’s infrastructure is built on hardened Linux appliances, drastically reducing attack vectors compared to traditional Windows-based software.
- Immutable cloud storage: In the Datto BCDR Cloud, backups are stored in write-once-read-many (WORM) format. This makes backup data immutable and unalterable, even if ransomware attempts to modify or delete it.
- Built-in ransomware detection: Machine learning powers Datto’s anomaly detection, automatically flagging suspicious changes in backup data before they can spread further. This early warning helps you act quickly and confidently.
- Automated backup verification: With automated screenshot verification, application service checks and sandbox recovery, Datto ensures backups are not only intact but fully recoverable.
- Rapid orchestration: Whether restoring a single virtual machine (VM) or orchestrating hundreds of systems, Datto enables fast, clean recoveries to minimize downtime and ensure operational continuity.
- Seamless MSP ecosystem integration: From Datto RMM and Autotask PSA to IT Glue and Datto EDR, Datto integrates into a complete IT ecosystem. This allows MSPs to coordinate responses more efficiently, streamline workflows and improve overall resilience.
Cyber insurance and compliance considerations
Cyber insurers are raising the bar. To qualify for coverage and ensure payouts when incidents occur, businesses must prove they have more than basic defenses in place. Requirements now often include immutable backups, tested recovery plans and clearly defined recovery time objectives (RTOs).
Recovery speed can even influence claim outcomes. For instance, if your recovery process takes 21 days but your policy only covers seven, the insurer may reduce or deny the claim entirely. That makes tested, reliable recovery a business necessity, not just an IT best practice.
Most cyber insurance policies today expect organizations to have:
- Documented incident response plans with DR runbooks, automated workflows, dependency maps and network configurations.
- Immutable, off-site and regularly tested backups that can withstand ransomware threats.
- Evidence of strong cyber hygiene practices, including regular end-user awareness training.
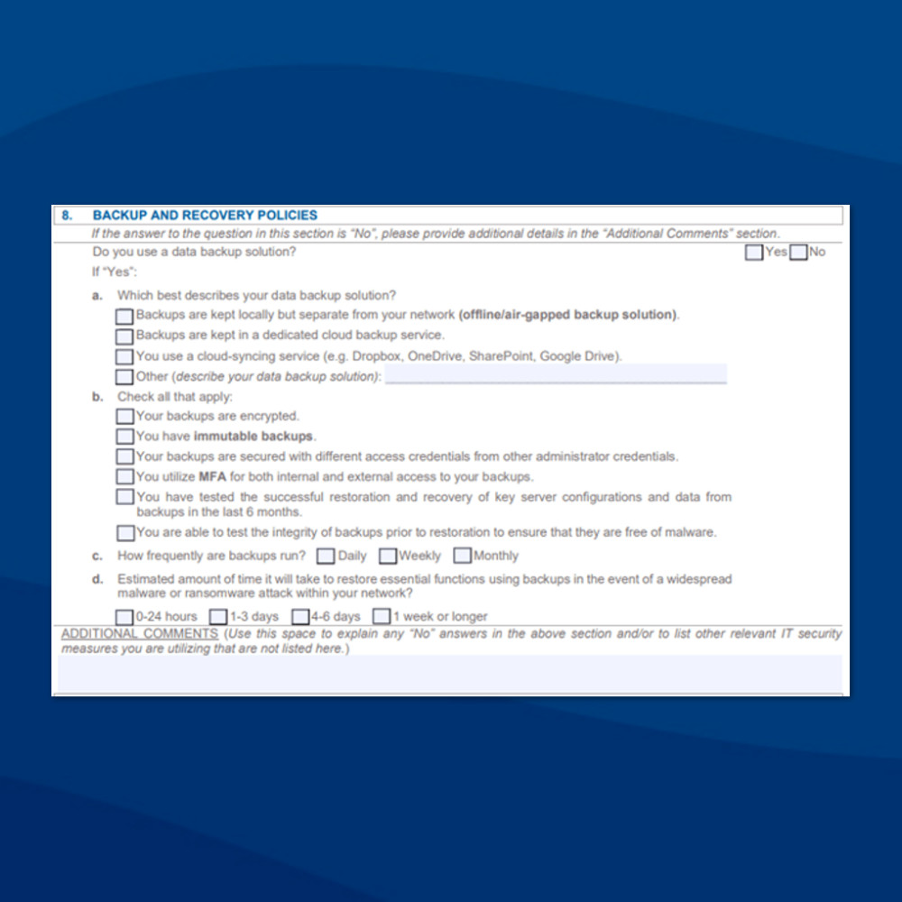
Fig 2: Example of a questionnaire in a cyber insurance application form
How MSPs can guarantee fast recovery for their clients
When ransomware strikes, recovery speed determines whether the outcome is a minor disruption or a full-scale crisis. To keep clients protected and operational, MSPs need to check off these four critical aspects:
Frequent backups to minimize data loss
Shorter recovery point objectives (RPOs) mean less data lost in an attack. By running frequent backups, MSPs give clients the ability to restore quickly without scrambling to recreate hours or days of work.
Immutable backups to keep data secure
Backups must be untouchable by ransomware. That means isolating them from production systems — such as using Linux-based backup appliances in Windows environments — and storing copies off-site in an immutable cloud storage. This ensures attackers cannot alter or delete recovery points, leaving MSPs with a clean copy when it matters most.
Virtualization to enable fast recovery
RTOs are just as critical as RPOs. Virtualization allows MSPs to restore operations in minutes, whether locally on backup devices, in the cloud when sites are compromised or through a hybrid approach that balances both.
Regular testing to build confidence
Backups only matter if they can be restored. Automated verification confirms recovery points are complete and bootable, while disaster recovery testing ensures systems, applications and dependencies can be restored in the right order. This guarantees that recovery is not just possible, but practical.
Ensuring business continuity in the age of ransomware
Ransomware is inevitable, but ransom payments and data loss don’t have to be. The key is building true ransomware resilience, where immutable backups, tested restore points and rapid recovery capabilities ensure that when an attack happens, you can bounce back quickly and confidently.
For MSPs managing multiple client environments, adopting Datto’s ransomware-resilient approach not only protects clients but also positions you as a trusted business continuity partner. And with our Partner Fast Track Offer, getting started is easier than ever. Leverage free-to-use hardware and additional benefits designed to accelerate your success.
Don’t wait for the next attack to test your defenses. Partner with Datto today and deliver the ransomware resilience your clients deserve.